Open Command and Control (OpenC2)
Creating a standardized language for the command and control of technologies that provide or support cyber defenses.

Vision
OpenC2 defines a language at a level of abstraction that will enable unambiguous command and control of cyber defense technologies.
OpenC2 is broad enough to provide flexibility in the implementation of devices and accommodate future products and will have the precision necessary to achieve the desired effect.
As an Open Source initiative, the community of cyber-security stakeholders across government agencies, small to large industries across all sectors, and academia can join together to innovate and evolve this cyberdefense approach.
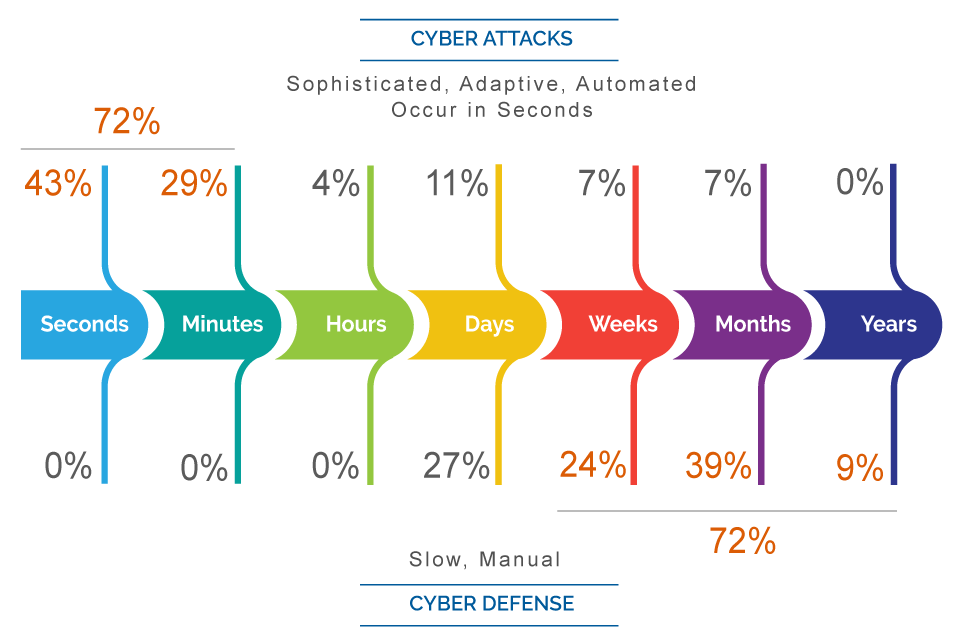
Current Cyberdefense
Today, cyber defense technologies, systems and applications often use proprietary software and commands to control system configurations. Most environments within a company or enterprise are comprised of hundreds of different types of cyber-defense devices. This highlights the importance of interconnecting an organization’s cybersecurity solutions to ensure ongoing and effective threat management.
When security incidents are detected or configuration changes are required, manual commands and real time system updates are required, increasing incident response time and potentially introducing human error.
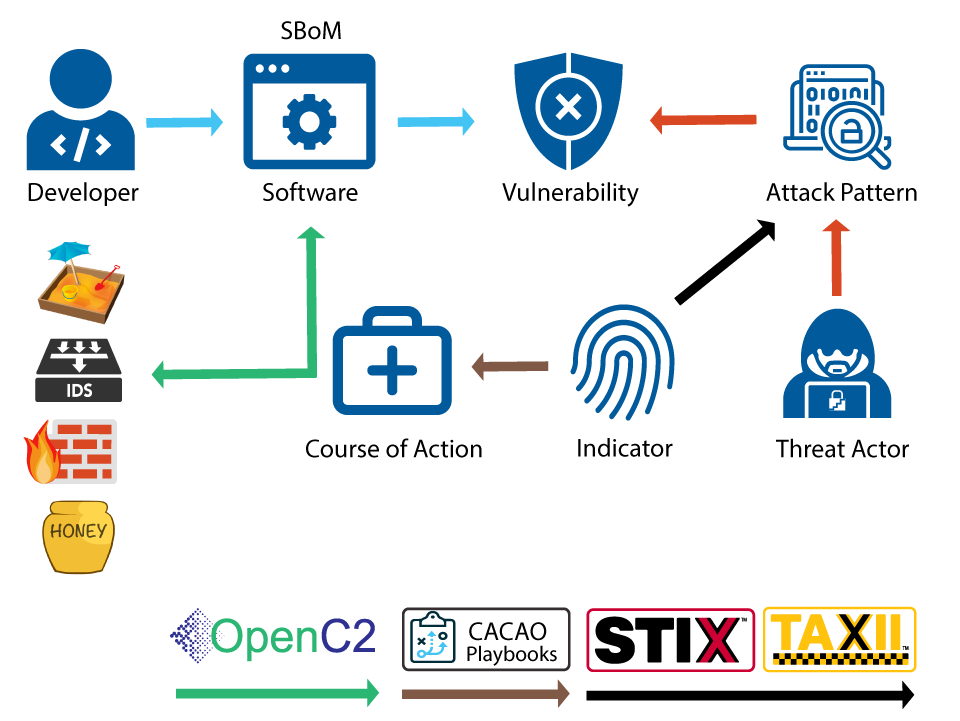
OpenC2 for Defense in Cyber-Relevant Time
Integrations reduce the level of manual efforts but are costly to develop and maintain and rely heavily on proprietary communication interfaces. This requires reconfiguring parts or the entire defense ecosystem of the organization when tools are introduced or replaced or when there are updates to the APIs utilized. Through OpenC2 and the use of standardized interfaces and protocols, interoperability across tools, vendors, technologies and programming languages is achieved.
Security professionals can orchestrate automated, tactical threat responses across a wide range of cyber-defense technologies at speeds significantly greater than previously imagined.
How can OpenC2 help?
OpenC2 is a limited language which simply conveys the “action” part of the cybersecurity process.
This open standards driven orchestration language, based on the nouns and verbs required to encode human intent and decisions and machine-readable instructions, enables automated courses of action.
Frequently Asked Questions
-
What is OpenC2??
OpenC2 is a standardized language for machine-to-machine communications for the command and control of technologies that provide or support cyber defenses. The OpenC2 Technical Committee is developing a suite of specifications that define the OpenC2 architecture, language, tailor its use to specific cyber-defense functions, and specify how to convey OpenC2 messages using various industry-standard transfer protocols.
-
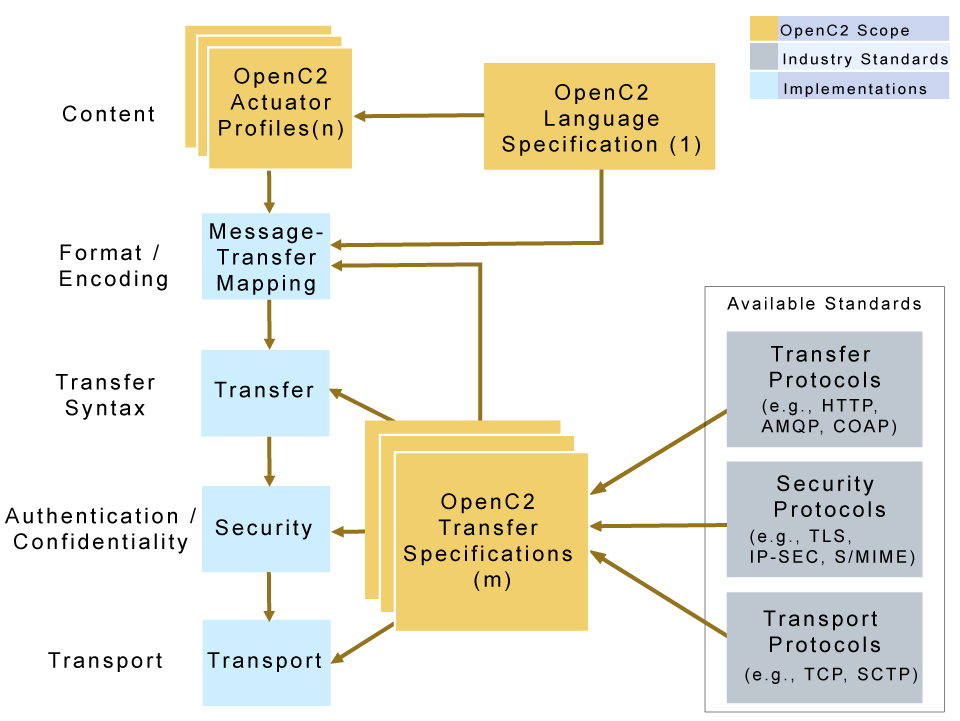
How is the "suite" of OpenC2 Specifications organized?
As described in the OpenC2 Architecture Specification, there are multiple types of OpenC2 specifications, meant to be used in concert:
-
The OpenC2 Architecture Specification describes the fundamental structures of OpenC2.
-
The OpenC2 Language Specification provides the essential elements of the language, the structure for Commands and Responses, and the mechanisms for extending the OpenC2 language.
-
OpenC2 Actuator Profiles specify the subset of the OpenC2 language relevant in the context of specific actuator functions (e.g., packet filtering, honeypots).
-
OpenC2 Transfer Specifications utilize existing protocols and standards (e.g., HTTPS, MQTT) to implement OpenC2 message transfer in specific environments.
-
-
What can OpenC2 do for me?
As cyber-defense technology vendors and providers adopt OpenC2, OpenC2 can dramatically improve incident response to cyber-threats and allow for enterprise wide interoperability for cyber-security policy orchestration. Management and development of cyber-defense responses is simplified and greater collaboration and integration across a wide range of technologies is enabled.
-
What is JADN?
JSON Abstract Data Notation (JADN) is a UML-based information modeling language that defines information requirements and data structure independently of data format. JADN was created by the OpenC2 TC to assist with defining OpenC2 information models for the language and actuator profiles in a way that supports the language's goal of enabling machine-to-machine communications for purposes of command and control of cyber defense components, subsystems and/or systems in a manner that is agnostic of the serialization formats.
-
How can I access OpenC2 and JADN?
OASIS Specifications are open for all to use. The TC's home page at OASIS lists the officially published specifications. This website includes a list of all OpenC2 specifications (published and under development), and a collection of open source software tooling to add in implementing OpenC2.